Cybersecurity - new page
We see cybersecurity as an enabler, not a blocker. Our approach lets you unlock competitive differentiators to help you win customers and we have a complete portfolio and broad expertise to help you do this.
Cybersecurity - Making you safer in a connected world
Cybersecurity has never been more relevant. With the potential of crippling ransomware attacks security and risk management leaders need to be able to define and address risks and threats in a new digital environment. Protecting your company and customers through cybersecurity is a business critical priority. Complex technologies, emerging threats and tight regulatory compliance demands a partner with global expertise.
Our portfolio of cybersecurity services has been specifically designed for organisations aiming for digital transformation, securely. Our focus is to bring you the capabilities you need to protect that transformed business.
How? By providing the expertise and global capability to deliver risk analysis, compliance checks, vulnerability tests, implementation of cyber technologies and managed security services.
Making Cybersecurity a Competitive Advantage
High growth companies see information security as an enabler of new business opportunities. focus on supporting business resiliency and responding to cyberattacks, including ransomware, denial-of-service outages and other types of attacks. Use better information security as a competitive differentiator to help win customers.
Create more value from cybersecurity by designing in security from the start and use it as springboard. To support wider organization initiatives.
Define
TEST BOTTOM PART
Protect
Defense
Our offerings
Compliance as a Service - Achieve continuous compliance and protection, effortlessly
We help you define, manage, and optimize your compliance processes so you can achieve:
- Continuous compliance with a broad array of industry standards and regulations
- Stringent governance
- Effective risk management
- Efficient monitoring and rationalization of internal controls
- Process efficiency and optimization to avoid unforced errors
- Higher productivity from internal staff
- Reduced costs and optimized capital allocation
- Continuous improvement in compliance and security-related processes
- More informed decision making
- Ability to embrace innovation and change
We offer three categories of CaaS services. Each category of services builds upon and adds value to the previous phase. Compliance as a Service offerings are delivered on-demand by compliance specialists at our Security Operations Centers in Luxembourg.
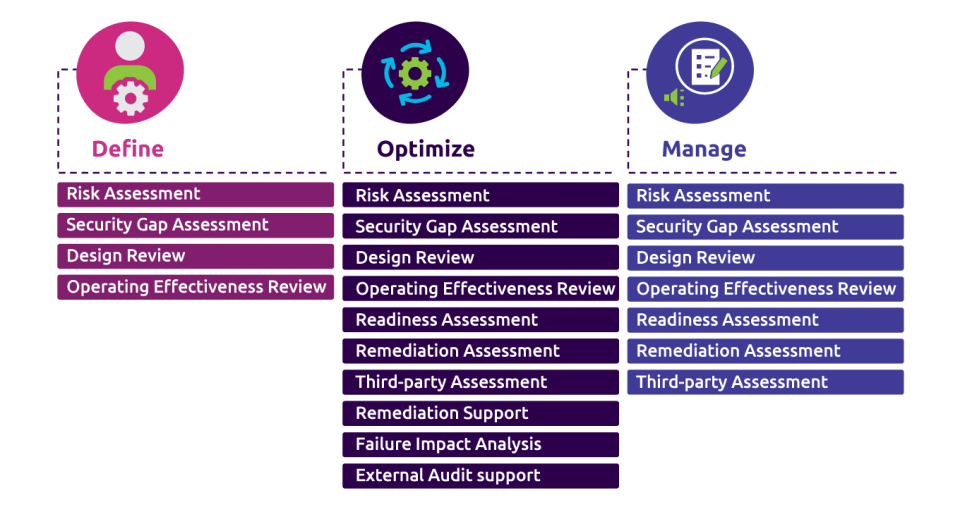
The net result: you can cut the cost, complexity, and heartburn of meeting compliance mandates while improving your organization’s security posture.
Our advantages
- Deep compliance experience: Capgemini compliance specialists are highly trained, certified, and have the right experience, tools and technologies.
- Industrialized services: Our services are industrialized from standardized processes, metrics and reporting, and we can meet your audit needs with consistent controls based on best practice frameworks and regulatory and industry requirements.
- Sector-specific compliance and cybersecurity experience: Capgemini has the breadth and depth of skills to cover compliance and security requirements in virtually every industry and market segment.
- Actionable threat intelligence: Our recommendations for improving your security posture are based on hard data points and multiple threat intelligence feeds collected and observed by our global network of SOCs.
- Advanced automation: Our automated workflows accelerate core processes, giving the efficiency and flexibility to meet peak demand and fast-changing priorities.
- Global scale : We deliver the compliance services you need, your way, anywhere in the world.
Cyberattack Simulation - The future of enterprise security is here
What’s getting through your defenses?
Are you under attack? Organizational, procedural and technical weaknesses are opening the door to increasingly sophisticated cyber attacks. A lack of security resource and limited knowledge of the toolsets being deployed by criminals to bypass the controls put in place pose a very real security risk. Even with security controls in place to test vulnerabilities, the hackers, committed professional criminals are breaching defenses.
A real-world approach to the cyber threat
The more you know about the threat’s your organization faces, the less vulnerable you are to increasingly sophisticated cyber attacks. We give you that knowledge. A Cyber Attack Simulation exercise exposes both known and unknown vulnerabilities by putting enterprise defenses under the same duress as in the real and evolving threat landscape. Leveraging our state-of-the-art Security Operations Center Lab, our proven methodologies span multiple technologies and security control areas, from physical security to personnel and procedural security controls, to system and application-level penetration.
Getting into the minds of cyber attackers
We think like a cyber attacker. Our approach goes beyond traditional penetration testing, which often excludes the very tactics, assets, or locations most valuable to attackers. We use information that is open source and available publicly to understand an attacker’s point of view. This enables us to quickly identify the security gaps in how an organization’s most valued assets are being protected. We look at every attack surface because we know the real-world cyber criminal will target any vulnerability.
Understand your threat position
Arrange a confidential Cyber Attack Simulation exercise now.
Cybersecurity Consulting - Strategic and Operational Consulting Services
Make Cybersecurity a Business Enabler in the Digital Enterprise.
With the growth in cyber attacks and data breaches costing business and the public sector millions every year, cybersecurity is high on the strategic agenda. Business leaders in both strategic and operational roles must answer vital questions:
- Is it possible to combine digital transformation with acceptable risks (i.e. while moving to the Cloud)?
- How do you transform your current IT security practices to be more data and customer-centric?
- Are you compliant with security / privacy regulations and corporate policies?
- Are your website, apps, data centres and data secured at best cost?
- Are security staff sufficient and trained enough?
- By putting in place proper cybersecurity assessments, your organisation can define the right strategy and transformation program to protect your sensitive data and assets.
Insight and strategy for effective cybersecurity and competitiveness
The more you know about your vulnerabilities and security controls, the more you can strengthen your organisation with effective procedures for governance, risk and compliance (GRC).
Our cybersecurity consulting services give you insight into your security management with assessments of your sensitive data, critical infrastructures and applications. We work with you to define and implement the right strategy, target operating model and GRC structure. We ensure your security design and operations support your strategic objectives and business continuity. By planning ahead with a cybersecurity strategy as part of your digital transformation journey, you will be in a more confident position to stay compliant and achieve cost savings. Our roadmap are built upon a very consistent framework (incl. market standards, human factor and economics).
Proven global expertise helps you transform securely
We have deep experience in cybersecurity transformation across financial services, utilities, manufacturing, government, and other sectors. Our consultants build a complete picture of your cybersecurity status and provide a clear vision of how to implement outcomes of Insight & Strategy phase. Based on market standards and referential (ISO, PCI, CoBIT, ISF, etc.) we help our clients to increase risk control (security and privacy) throughout proper change management process including economics and staff professionalisation. to improve it. We partner with leading security vendors to ensure you benefit from the latest tools and technologies to safeguard your enterprise assets (IAM, SIEM, DLP, etc.).
Cybersecurity Defense Maturity Evaluation - Operationally focused Cybersecurity Assessment
Measure the effectiveness of your organization, capabilities and operations. Know where you stand so you can identify gaps and develop plans to increase effectiveness across the entire enterprise.
The most effective way to thwart targeted, sophisticated and persistent cyber threats is to have a mature cyber-defense program. Capgemini’s Cybersecurity Defense Maturity Evaluation measures an organization’s alignment to the Unified Enterprise Defense strategy across 13 key evaluation domains and sub-components, to quantify an organization’s cybersecurity defensive posture.
Capgemini’s Cyber Defense Maturity Evaluation is a repeatable benchmark of an organizations cybersecurity maturity.The evaluation integrates evidence-based approaches and frameworks such as ISO, NIST and CMMI into the Capgemini Unified Enterprise Defense strategy. This strategy drives a comprehensive evaluation for how an organization both protects and defends the enterprise through proper visibility and effective leverage of threat intelligence.
Built on our Unified Enterprise Defense Strategy
The Unified Enterprise Defense structure was developed by Capgemini to outline and characterize all of the important elements that an organization must develop and integrate cohesively, to have an effective strategy for protecting and defending an enterprise from all cybersecurity threats.
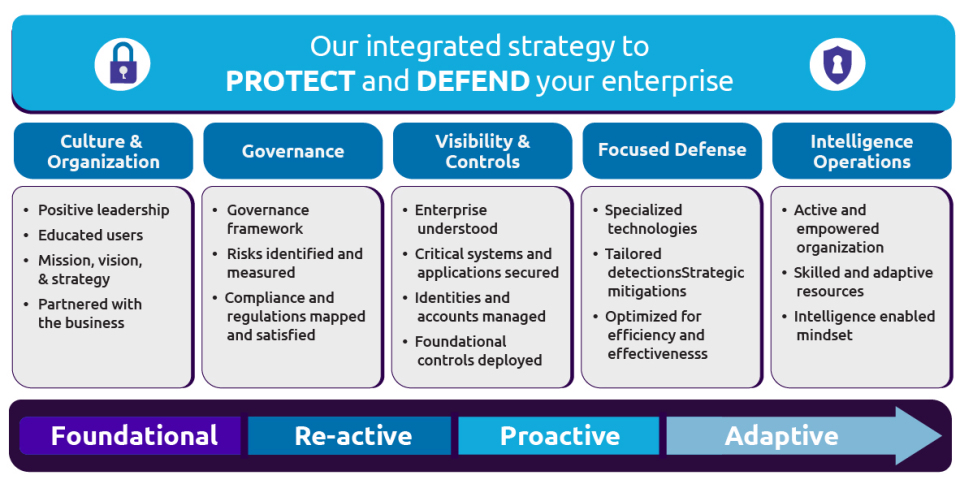
Cybersecurity maturity using a Unified Enterprise Defense Strategy
When it comes to cybersecurity maturity, organizations often find themselves straddling multiple levels in a cybersecurity maturity model. This model spans four major states; Foundational, Reactive, Proactive and Adaptive. Using these states as a measurement scale Capgemini’s Cybersecurity Defense Maturity Evaluation evaluates 13 domains with an emphasis on the following cybersecurity functions:
- Emerging security capabilities – The enterprise has started to build out capabilities for foundational areas of security aligned to risk. Operations take place in a distributed manner, and a standardized model and consistent approach have not been defined and do not focus on network defense functions.
- Defined security operations – The enterprise has a baseline of repeatable security operations and may have a dedicated team for network defense. Workloads are cyber response activities, preventing effective defensive operations. Threat intelligence may be leveraged in an ad-hoc capacity.
- Integrated defensive operations – The enterprise has aligned both aspects of securing the enterprise and defending the enterprise into a well-defined industry model. Threat intelligence is integral to daily operations and feeds detective and defensive strategies.
- Adaptive intelligence operations – The enterprise has established a mature cyber defense program. Operations continue to mature and adapt through automation efficiencies and partnerships as the threat landscape changes. Custom capabilities are established and threat intelligence managed to the degree that historical data trending enables the security organization to stay ahead of adversaries.
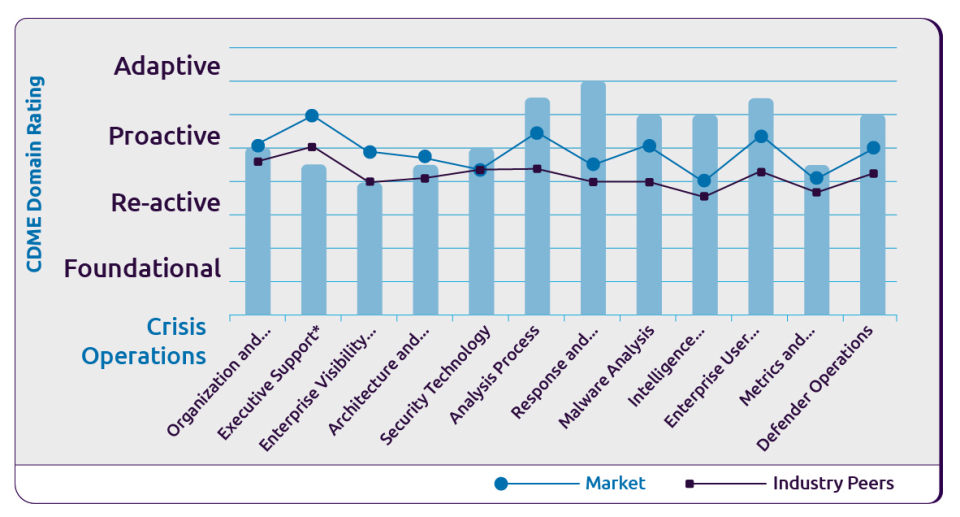
The output of the Cybersecurity Defense Maturity Evaluation enables an organization to focus its attention on specific cybersecurity gaps based on comparison to the benchmark itself, peer behaviors and the market in general. We deliver recommendations on how to address the exposed gaps and increase overall maturity.
Through the application of a repeatable and process driven collection of intelligence, the Cyber Defense Maturity Evaluation provides organizations an understanding of their existing cybersecurity posture, visibility to and providing a plan for addressing gaps along with a benchmark capability to continually measure their cybersecurity effectiveness.
Benefits
- Operationally focused – our recommendations provide immediate improvements
- Detailed analysis – moving beyond “checkbox” compliance
- Measuring effectiveness and benchmarking – both against your peers and the industry at large
- Repeatable and adaptable methodology – shows year over year growth
- Continuous evolution of benchmarks – reflects leading best practices and evolving market experience
Data Protection & GDPR
The data protection landscape is rapidly changing. As organizations harness the power offered by Digital and personal data, increasingly smart cybercriminals are intent on stealing or compromising that data. Compliance with the EU’s GDPR (General Data Protection Regulation) from May 2018 is thus both a regulatory requirement, a risk management issue and a strategic business imperative.
Avoid the risk of GDPR non-compliance
The EU’s GDPR represents a comprehensive reform of existing data protection laws. It requires a significant change in the way organizations manage personal data in today’s digital operating environment. GDPR encompasses data management and security, including new concepts – transparency and accountability – and a key requirement to notify data breaches. Non-compliance could lead to fines of 4% of an organization’s worldwide turnover or 20 million euro – whichever is higher. Be ready to demonstrate you take appropriate practices to protect personal data.
A consistent GDPR roadmap with operational outcomes
As part of its Global GDPR services, Capgemini proposes advisory and technology solutions which are applicable to existing, legacy and new digital systems to address the key aspects of Data Privacy and Security:
- Data Protection Assessments and Program Management
- Data Discovery and Data Minimization / Pseudonymization
- Data and Database Encryption
- Identity and Access Management
- Security Operation Centers and Data Leak Prevention
- GDPR Assurance Services
Drawing on global experience across diverse industries
We also work with Data Protection Officers to set out the roles, organization, and IT requirements for protecting data assets (at rest, in motion, in use) and meeting GDPR requirements
With end-to-end data protection capabilities, Capgemini has a deep understanding of the GDPR, its associated business issues, and relevant technology solutions. We help CIO, CISO, DPO, CDO and DMO from all around the world meet GDPR requirements while building digital trust with automated solutions.
Manage your risk and compliance effectively
Enhance your reputation and ensure compliance through real-time monitoring and analysis
The challenge of a complex GRC process
An effective GRC regime is essential in today’s business world, but can be challenging to implement. GRC processes operate in silos at many companies, creating a multiplicity of frameworks and systems.
This can result in:
- Poor understanding of financial, operational, IT, regulatory, and fraud risks.
- Ineffective risk minimization.
- Exposure to fines, penalties and litigation.
- High GRC costs.
- Possibility of stakeholder backlash.
- Weak financial statements.
A GRC framework that shifts overhead cost to value driver
Our GRC solutions combine real-time monitoring, reporting, and analysis to help companies comply with regulations and prepare for unexpected events. GRC focuses on three key services to address specific, high-profile business challenges around risk governance and GRC security. These services are:
- Regulatory Compliance
- IT Risk & Compliance
- Continuous Control Monitoring
The benefits of our GRC platform
The tools that make up our GRC offering can form part of a enterprise risk management framework that delivers:
- Minimize risk by aggressively identifying and addressing potential risk.
- Strengthen compliance through regular audit and control monitoring activities.
- Increase profitability by reducing compliance costs and leakage.
- Enhance reputation by adhering to compliance requirements.
Penetration Testing, Red Teaming, and Threat Simulation - Think like an adversary, be a defender
Understand your environment and validate the effectiveness of your technical controls while enabling your organization to gain real world experience defending your enterprise from current threats and adversaries.
Penetration Testing
Capgemini conducts a full suite of technical testing to validate the effectiveness of controls and determine the integrity or configuration of a network, system, or application. Capgemini is experienced in conducting testing within critical operational environments, heavily regulated industries, and on a wide variety of devices and systems. Our testers will partner with you to understand your needs and objectives, whether they are driven by compliance and regulations or simply a desire to be as secure as possible, and then build the appropriate test scenarios. Through our rigorous adherence to the predefined “Rules of Engagement”, we will ensure there are no impacts to your operations or business. Based on the findings of our assessment and testing, we make recommendations for specific mitigations to reduce risks and prevent incidents in an organization’s business and operational environment.
Red Teaming and Threat Simulation
Well architected networks, effective controls, and secure configurations are all important contributing factors to your cybersecurity posture. However, without the proper visibility, skillsets, and processes your capabilities are incomplete. Capgemini’s Red Teaming and Threat Simulations will assess how your people, processes, and technology are working together to actively defend your enterprise. These solutions will enable you to better understand your detection, response, and analysis capabilities, and highlight tactical and strategic mitigation opportunities to ensure more effective defense in depth across the entire threat spectrum. Our Capgemini testers will work with you to understand your threat profile, identify areas of concern and interest, and partner with you to establish a series of engagements and interactive scenarios designed to confirm your capabilities are operating as intended and then push your organization to the limit. The result will be educational for both you and your team, providing actionable insights and observations to improve your overall security posture.
Identity & Access Management
Adopting social, mobility, analytics, cloud and Internet of Things (SMACT) technologies as part of your digital transformation doesn’t have to mean new risks to sensitive data and other assets.
With our Identity and Access Management (IAM) services, you can manage cyber security risks and gain control of new ways of working.
Your First Line of Cyber Defense
As you connect with more and more customers, business partners and third-parties, the identity scope of your business will expand in parallel.
Our recent findings show that 84% of organizations see the ability to support different types of access management such as alternative authentication methods and social logins as high priority. Yet only 21% feel equipped with such solutions for adaptive authentication.
Your IAM infrastructure will become the new front door through which they gain access to your corporate resources. Its efficiency and effectiveness will be critical to business operations and a cornerstone of your cybersecurity. It must protect your assets as employees using multiple devices from any location seek access to work-related applications.
IAM should be your first line of cyber defense to stay protected.
Right People, Right Resources, Right Time
IAM is a crucial business enabler. With it, you can secure the sharing of identity information between new consumer-facing applications, control internal risks, and protect your enterprise against cyber attacks. This means that the right people get access to the right resources at the right time.
Our transformative approach works with the right people in your business to ensure a successful IAM implementation.
We help you define your IAM strategy and provide these services:
- User registration and authentication
- Managing user rights
- Controlling access to resources
- Auditing user activities
Global IAM Expertise that Makes Digital Transformation Happen
More than 40 major IAM assignments globally in the past five years have given us unique insight into the IAM landscape. Organizations have already chosen to work with us to understand their IAM challenges and develop their vision, strategy, business alignment and business case.
We partner with all major IAM vendors and undertake the business change, technical implementation and integration of the best IAM solution for the individual needs of each client. We make IAM happen as part of a balanced, pragmatic approach to protecting digital assets.
Endpoint Security - Future Ready Endpoint Protection as a Service
Traditional anti-virus end-point security is no longer powerful enough to safeguard today’s digital enterprise.
More endpoints require more security
Research reveals that 71% of breaches target user devices. At the same time, employees expect to be able to work on their laptops, tablets and smartphones, and to use them to access corporate networks. The challenge is thus to find new ways to ensure today’s digital workforce can work on any device without comprising corporate assets.
Responding to incidents – fast
Poor insight and analytics often limit detection capabilities when a breach occurs. This leaves data assets and systems vulnerable to hackers for too long. Capgemini’s comprehensive Future Ready Endpoint Protection as Service (EPaaS) provides a rapid incident response to prevent attacks from spreading.
Security tailored to your needs
We know that every organization has its own approach to managing cybersecurity aligned with specific business strategies and risk profiles. That’s why our Future Ready EPaaS is tailored to the unique needs of each client, from the services themselves, to our flexible deployment models.
One-of-a-kind security offering
Our philosophy is to ‘think like an attacker’. A mindset of continuous innovation ensures we are always looking for ways to improve visibility, de-obfuscation and behavioral detection on endpoints.
Capgemini’s EPaaS monitors, detects, responds and protects with a solution and security strategy aligned to your business priorities.
Cloud Security - Secure your end-to-end cloud journey
Pragmatic cybersecurity approaches and services can support your ongoing cloud evolution.
Have you got the complete picture?
Multiple cloud solutions, hybrid environments and ecosystem complexity mean that very few organizations have a complete grasp of their cloud security posture. Organizations are struggling to address security challenges around identity and access control, monitoring and responding to threats, data leakage, governance, security skills shortages, and shadow IT adoption.
Secure your end-to-end cloud journey
Capgemini helps you respond to these security concerns with a complete portfolio of advisory, stand-alone and end-to-end Managed Security Services. We have the capability, scale and global reach required to provide you with everything you need in one place to effectively manage your security across a hybrid cloud IT estate.
Whether you are just starting out on your migration to cloud, are re-evaluating the cloud architecture you’ve built, or have already reached a mature, agile DevSecOps position, Capgemini can help.
- We Assess. A Cloud Security Assessment provides you with insight into your current or planned adoption of cloud computing.
- We Advise. Our Cloud Security Advisory services are based on more than a decade of helping clients adopt cloud security.
- We Implement. Our Cloud Protection Services offer a range of solutions for identity and access management, data protection, application security and infrastructure security.
- We Operate. To ensure the security of your cloud-based operations, our Cloud Security Monitoring solution makes security monitoring a key foundation of your cloud architecture. Our Cloud Security Services are delivered from our global network of ISO27001-certified security operations centers (SOCs) and can be accessed either via our wider Capgemini Cloud Platform (CCP), or as standalone services.
Better cloud security outcomes
Our global network of 24/7 SOCs ensures you can rapidly ramp up your cloud security as it’s needed, delivering secure, global cloud scalability. Our agnosticism means you can seamlessly integrate security across diverse technologies and cloud platforms, including AWS, Azure and Google. Consumption-based pricing reduces the cost of cloud ownership and our as-a-service delivery model allows you to choose only what you need, when you need it.
With our philosophy to ‘think like an attacker’, we protect our clients through a combination of threat intelligence, robust architectures and a highly industrialized and automated service delivery model. We test and incorporate the latest security features in our solutions, and we keep our clients compliant with data protection and security regulations, such as PCI DSS, HIPAA and GDPR as required.
Cyber Defense Center
Almost all organizations will experience a data security breach this year. It’s how you respond that makes all the difference.
Our network of connected 24/7 Cyber Defense Centers (CDCs) gives you the resources and skills you need to counter the threat – fast.
A new generation of cybersecurity
It takes an average 99 days* for a malicious attack to be identified. In the meantime, data privacy and protection have become core to today’s security strategies: data fuels business success. It’s clear that a new generation of cybersecurity is needed. Even if you are well protected with the right tools and the right processes in place, you still leave yourself open to attack if you are not monitoring systems; detecting potential security incidents; and able to make changes to your operations quickly when a threat is detected.
Understanding and assessing your risks
We recognize that every enterprise has its own unique security requirements based on the market and market segment they operate in. That’s why we always begin by helping our clients understand and quantify their risk profiles, identify critical data assets, and assess their current security strategies and levels of protection. Only then will we tailor the end-to-end services delivered through our proven Cyber defense center (CDC) model to each client’s specific context and business ambitions.
Your security; your choice of delivery model
There is no one-size-fits all approach to cybersecurity. So, our services are offered though different delivery modes based on the information we gather about your security needs – a Dedicated SOC, a Managed SOC, or our Hybrid model. Our network of global CDCs stretches across the world, with CDCs in India, Europe and North America complemented by satellite CDCs. They collaborate, share expertise and best practices, and communicate success stories in their relentless pursuit of robust cybersecurity.
Threat intelligence and regulatory compliance
We use data to turn our clients from the hunted into the threat hunters. We bring together SIEM, network security monitoring, endpoints monitoring, payload analysis and offline big data analytics in an intelligence-driven approach. This incorporates a broad range of threat intelligence sources, allied with industry-leading analytics capabilities. We then use the data to align a client’s required cybersecurity actions with the specific needs of each market in which they are active.
We also help clients comply with regulatory changes relating to security, including Europe’s NIS Directive, the EU’s GDPR, and New York State Department of Financial Services regulations in the US.
*Mandiant (a FireEye company), M-Trends 2017 report
Managed Detection and Response
Early detection and proactive response for incident prevention.
Partner with Capgemini to tackle one of the most difficult challenges facing cybersecurity organizations today – incident prevention. We function as an embedded partner with our clients to maximize enterprise visibility, generate contextual intelligence and direct incident response and prevention strategies.
Capgemini’s Managed Detection and Response Service
Capgemini’s Managed Detection and Response (MDR) service is a new breed of solution that delivers advanced monitoring, detection, and response capabilities. Capgemini’s MDR goes beyond traditional MSSP or IR services to provide a continuous end-to-end approach that detects malicious threats earlier, provides comprehensive analysis of the intrusion faster, and delivers actionable guidance for future prevention based on intelligence gained every time.
The MDR service includes:
- World-class cyber-intelligence analysts supporting your team
- Implementation of consistent and repeatable analysis framework added to operating procedures
- Biweekly, non-customer-specific threat intel summary
- Timely reports include:
- Escalated events with detailed, actionable analysis and prioritized recommendations
- Details of analyst investigations that do not result in an actionable escalated events
- Summary of service outcomes, trend analysis, and continuous improvement metrics and recommendations
Why Capgemini?
For nearly two decades we have protected our enterprise and the cyber footprint of our clients worldwide with enhanced visibility and advanced human analysis. We continually monitor cyber-landscape trends and adapt our approach to outpace cyber-threat actors to defend both our interests and those of our clients.
MDR service benefits:
- Improve situational awareness with maximum visibility and continuous monitoring
- Reduce distracting false positives and costly false negatives
- Prevent breaches through earlier detection and more effective responses
- Gain contextual intelligence to outpace adversaries and maintain your defensive advantage
The cybersecurity market is shifting. Today’s ever-evolving threat landscape is driving organizations to change how they address incident prevention.
The best incident prevention strategy starts with smarter detection for faster response.
Our offerings
Define
Compliance as a Service - Achieve continuous compliance and protection, effortlessly
We help you define, manage, and optimize your compliance processes so you can achieve:
- Continuous compliance with a broad array of industry standards and regulations
- Stringent governance
- Effective risk management
- Efficient monitoring and rationalization of internal controls
- Process efficiency and optimization to avoid unforced errors
- Higher productivity from internal staff
- Reduced costs and optimized capital allocation
- Continuous improvement in compliance and security-related processes
- More informed decision making
- Ability to embrace innovation and change
We offer three categories of CaaS services. Each category of services builds upon and adds value to the previous phase. Compliance as a Service offerings are delivered on-demand by compliance specialists at our Security Operations Centers in Luxembourg.

The net result: you can cut the cost, complexity, and heartburn of meeting compliance mandates while improving your organization’s security posture.
Our advantages
- Deep compliance experience: Capgemini compliance specialists are highly trained, certified, and have the right experience, tools and technologies.
- Industrialized services: Our services are industrialized from standardized processes, metrics and reporting, and we can meet your audit needs with consistent controls based on best practice frameworks and regulatory and industry requirements.
- Sector-specific compliance and cybersecurity experience: Capgemini has the breadth and depth of skills to cover compliance and security requirements in virtually every industry and market segment.
- Actionable threat intelligence: Our recommendations for improving your security posture are based on hard data points and multiple threat intelligence feeds collected and observed by our global network of SOCs.
- Advanced automation: Our automated workflows accelerate core processes, giving the efficiency and flexibility to meet peak demand and fast-changing priorities.
- Global scale : We deliver the compliance services you need, your way, anywhere in the world.
Cyberattack Simulation - The future of enterprise security is here
What’s getting through your defenses?
Are you under attack? Organizational, procedural and technical weaknesses are opening the door to increasingly sophisticated cyber attacks. A lack of security resource and limited knowledge of the toolsets being deployed by criminals to bypass the controls put in place pose a very real security risk. Even with security controls in place to test vulnerabilities, the hackers, committed professional criminals are breaching defenses.
A real-world approach to the cyber threat
The more you know about the threat’s your organization faces, the less vulnerable you are to increasingly sophisticated cyber attacks. We give you that knowledge. A Cyber Attack Simulation exercise exposes both known and unknown vulnerabilities by putting enterprise defenses under the same duress as in the real and evolving threat landscape. Leveraging our state-of-the-art Security Operations Center Lab, our proven methodologies span multiple technologies and security control areas, from physical security to personnel and procedural security controls, to system and application-level penetration.
Getting into the minds of cyber attackers
We think like a cyber attacker. Our approach goes beyond traditional penetration testing, which often excludes the very tactics, assets, or locations most valuable to attackers. We use information that is open source and available publicly to understand an attacker’s point of view. This enables us to quickly identify the security gaps in how an organization’s most valued assets are being protected. We look at every attack surface because we know the real-world cyber criminal will target any vulnerability.
Understand your threat position
Arrange a confidential Cyber Attack Simulation exercise now.
Cybersecurity Consulting - Strategic and Operational Consulting Services
Make Cybersecurity a Business Enabler in the Digital Enterprise.
With the growth in cyber attacks and data breaches costing business and the public sector millions every year, cybersecurity is high on the strategic agenda. Business leaders in both strategic and operational roles must answer vital questions:
- Is it possible to combine digital transformation with acceptable risks (i.e. while moving to the Cloud)?
- How do you transform your current IT security practices to be more data and customer-centric?
- Are you compliant with security / privacy regulations and corporate policies?
- Are your website, apps, data centres and data secured at best cost?
- Are security staff sufficient and trained enough?
- By putting in place proper cybersecurity assessments, your organisation can define the right strategy and transformation program to protect your sensitive data and assets.
Insight and strategy for effective cybersecurity and competitiveness
The more you know about your vulnerabilities and security controls, the more you can strengthen your organisation with effective procedures for governance, risk and compliance (GRC).
Our cybersecurity consulting services give you insight into your security management with assessments of your sensitive data, critical infrastructures and applications. We work with you to define and implement the right strategy, target operating model and GRC structure. We ensure your security design and operations support your strategic objectives and business continuity. By planning ahead with a cybersecurity strategy as part of your digital transformation journey, you will be in a more confident position to stay compliant and achieve cost savings. Our roadmap are built upon a very consistent framework (incl. market standards, human factor and economics).
Proven global expertise helps you transform securely
We have deep experience in cybersecurity transformation across financial services, utilities, manufacturing, government, and other sectors. Our consultants build a complete picture of your cybersecurity status and provide a clear vision of how to implement outcomes of Insight & Strategy phase. Based on market standards and referential (ISO, PCI, CoBIT, ISF, etc.) we help our clients to increase risk control (security and privacy) throughout proper change management process including economics and staff professionalisation. to improve it. We partner with leading security vendors to ensure you benefit from the latest tools and technologies to safeguard your enterprise assets (IAM, SIEM, DLP, etc.).
Cybersecurity Defense Maturity Evaluation - Operationally focused Cybersecurity Assessment
Measure the effectiveness of your organization, capabilities and operations. Know where you stand so you can identify gaps and develop plans to increase effectiveness across the entire enterprise.
The most effective way to thwart targeted, sophisticated and persistent cyber threats is to have a mature cyber-defense program. Capgemini’s Cybersecurity Defense Maturity Evaluation measures an organization’s alignment to the Unified Enterprise Defense strategy across 13 key evaluation domains and sub-components, to quantify an organization’s cybersecurity defensive posture.
Capgemini’s Cyber Defense Maturity Evaluation is a repeatable benchmark of an organizations cybersecurity maturity.The evaluation integrates evidence-based approaches and frameworks such as ISO, NIST and CMMI into the Capgemini Unified Enterprise Defense strategy. This strategy drives a comprehensive evaluation for how an organization both protects and defends the enterprise through proper visibility and effective leverage of threat intelligence.
Built on our Unified Enterprise Defense Strategy
The Unified Enterprise Defense structure was developed by Capgemini to outline and characterize all of the important elements that an organization must develop and integrate cohesively, to have an effective strategy for protecting and defending an enterprise from all cybersecurity threats.

Cybersecurity maturity using a Unified Enterprise Defense Strategy
When it comes to cybersecurity maturity, organizations often find themselves straddling multiple levels in a cybersecurity maturity model. This model spans four major states; Foundational, Reactive, Proactive and Adaptive. Using these states as a measurement scale Capgemini’s Cybersecurity Defense Maturity Evaluation evaluates 13 domains with an emphasis on the following cybersecurity functions:
- Emerging security capabilities – The enterprise has started to build out capabilities for foundational areas of security aligned to risk. Operations take place in a distributed manner, and a standardized model and consistent approach have not been defined and do not focus on network defense functions.
- Defined security operations – The enterprise has a baseline of repeatable security operations and may have a dedicated team for network defense. Workloads are cyber response activities, preventing effective defensive operations. Threat intelligence may be leveraged in an ad-hoc capacity.
- Integrated defensive operations – The enterprise has aligned both aspects of securing the enterprise and defending the enterprise into a well-defined industry model. Threat intelligence is integral to daily operations and feeds detective and defensive strategies.
- Adaptive intelligence operations – The enterprise has established a mature cyber defense program. Operations continue to mature and adapt through automation efficiencies and partnerships as the threat landscape changes. Custom capabilities are established and threat intelligence managed to the degree that historical data trending enables the security organization to stay ahead of adversaries.
The output of the Cybersecurity Defense Maturity Evaluation enables an organization to focus its attention on specific cybersecurity gaps based on comparison to the benchmark itself, peer behaviors and the market in general. We deliver recommendations on how to address the exposed gaps and increase overall maturity.
Through the application of a repeatable and process driven collection of intelligence, the Cyber Defense Maturity Evaluation provides organizations an understanding of their existing cybersecurity posture, visibility to and providing a plan for addressing gaps along with a benchmark capability to continually measure their cybersecurity effectiveness.

Benefits
- Operationally focused – our recommendations provide immediate improvements
- Detailed analysis – moving beyond “checkbox” compliance
- Measuring effectiveness and benchmarking – both against your peers and the industry at large
- Repeatable and adaptable methodology – shows year over year growth
- Continuous evolution of benchmarks – reflects leading best practices and evolving market experience
Data Protection & GDPR
The data protection landscape is rapidly changing. As organizations harness the power offered by Digital and personal data, increasingly smart cybercriminals are intent on stealing or compromising that data. Compliance with the EU’s GDPR (General Data Protection Regulation) from May 2018 is thus both a regulatory requirement, a risk management issue and a strategic business imperative.
Avoid the risk of GDPR non-compliance
The EU’s GDPR represents a comprehensive reform of existing data protection laws. It requires a significant change in the way organizations manage personal data in today’s digital operating environment. GDPR encompasses data management and security, including new concepts – transparency and accountability – and a key requirement to notify data breaches. Non-compliance could lead to fines of 4% of an organization’s worldwide turnover or 20 million euro – whichever is higher. Be ready to demonstrate you take appropriate practices to protect personal data.
A consistent GDPR roadmap with operational outcomes
As part of its Global GDPR services, Capgemini proposes advisory and technology solutions which are applicable to existing, legacy and new digital systems to address the key aspects of Data Privacy and Security:
- Data Protection Assessments and Program Management
- Data Discovery and Data Minimization / Pseudonymization
- Data and Database Encryption
- Identity and Access Management
- Security Operation Centers and Data Leak Prevention
- GDPR Assurance Services
Drawing on global experience across diverse industries
We also work with Data Protection Officers to set out the roles, organization, and IT requirements for protecting data assets (at rest, in motion, in use) and meeting GDPR requirements
With end-to-end data protection capabilities, Capgemini has a deep understanding of the GDPR, its associated business issues, and relevant technology solutions. We help CIO, CISO, DPO, CDO and DMO from all around the world meet GDPR requirements while building digital trust with automated solutions.
Manage your risk and compliance effectively
Enhance your reputation and ensure compliance through real-time monitoring and analysis
The challenge of a complex GRC process
An effective GRC regime is essential in today’s business world, but can be challenging to implement. GRC processes operate in silos at many companies, creating a multiplicity of frameworks and systems.
This can result in:
- Poor understanding of financial, operational, IT, regulatory, and fraud risks.
- Ineffective risk minimization.
- Exposure to fines, penalties and litigation.
- High GRC costs.
- Possibility of stakeholder backlash.
- Weak financial statements.
A GRC framework that shifts overhead cost to value driver
Our GRC solutions combine real-time monitoring, reporting, and analysis to help companies comply with regulations and prepare for unexpected events. GRC focuses on three key services to address specific, high-profile business challenges around risk governance and GRC security. These services are:
- Regulatory Compliance
- IT Risk & Compliance
- Continuous Control Monitoring
The benefits of our GRC platform
The tools that make up our GRC offering can form part of a enterprise risk management framework that delivers:
- Minimize risk by aggressively identifying and addressing potential risk.
- Strengthen compliance through regular audit and control monitoring activities.
- Increase profitability by reducing compliance costs and leakage.
- Enhance reputation by adhering to compliance requirements.
Penetration Testing, Red Teaming, and Threat Simulation - Think like an adversary, be a defender
Understand your environment and validate the effectiveness of your technical controls while enabling your organization to gain real world experience defending your enterprise from current threats and adversaries.
Penetration Testing
Capgemini conducts a full suite of technical testing to validate the effectiveness of controls and determine the integrity or configuration of a network, system, or application. Capgemini is experienced in conducting testing within critical operational environments, heavily regulated industries, and on a wide variety of devices and systems. Our testers will partner with you to understand your needs and objectives, whether they are driven by compliance and regulations or simply a desire to be as secure as possible, and then build the appropriate test scenarios. Through our rigorous adherence to the predefined “Rules of Engagement”, we will ensure there are no impacts to your operations or business. Based on the findings of our assessment and testing, we make recommendations for specific mitigations to reduce risks and prevent incidents in an organization’s business and operational environment.
Red Teaming and Threat Simulation
Well architected networks, effective controls, and secure configurations are all important contributing factors to your cybersecurity posture. However, without the proper visibility, skillsets, and processes your capabilities are incomplete. Capgemini’s Red Teaming and Threat Simulations will assess how your people, processes, and technology are working together to actively defend your enterprise. These solutions will enable you to better understand your detection, response, and analysis capabilities, and highlight tactical and strategic mitigation opportunities to ensure more effective defense in depth across the entire threat spectrum. Our Capgemini testers will work with you to understand your threat profile, identify areas of concern and interest, and partner with you to establish a series of engagements and interactive scenarios designed to confirm your capabilities are operating as intended and then push your organization to the limit. The result will be educational for both you and your team, providing actionable insights and observations to improve your overall security posture.
Featured Insights




